Redundancy via KVM technology keeps critical systems accessible
The proliferation of computers and IT-based systems in industrial process automation has created a need for advanced and flexible system access to these computers. This digitalization trend creates a significant demand for more data to be managed, monitored, secured and evaluated.
In turn, organizations are implementing redundancy approaches through keyboard-video-mouse (KVM) technology to ensure critical systems are available and instantly accessible to any authorized user.
KVM refers to the interfaces of a computer. KVM devices help separate computers and their users. Operators instead access, extend, switch or distribute computer signals using dedicated CAT cables, optical fibers or standard IP-based network infrastructures and provide them again at the remote workplace in high resolution and with imperceptible latency. That allows for the implementation of comprehensive redundancy concepts for security-relevant and mission-critical applications.
KVM components explained. Fundamental KVM equipment includes extenders, switches and matrix systems. KVM extenders expand computer signals 1:1. KVM switches enable a 1:n connection (i.e., several computers can be operated using fewer peripherals from one console). If several workplaces access several computers simultaneously as an n:m connection, the installation becomes even more flexible. KVM matrix systems, which can flexibly map even the largest IT installations, offer this possibility.
Matrix systems consist of three components:
- Computer modules (CPUs), which forward signals from computers to a matrix
- A central module, which connects user consoles and computers
- Console modules (CONs) to connect the consoles on which users work.
KVM systems enable the operation of multiple computers remotely in real time, without software installation, and independent of the operating system, thus saving peripherals. One of the main advantages of using KVM equipment is the simple implementation of security concepts. The computers are in a central, air-conditioned server room, protecting them from unauthorized access. KVM systems can be used to implement a variety of redundancy concepts to increase cybersecurity significantly. Redundancies also enable operators to switch to a redundant system even if a line or system component fails. Thus, they can continue their work immediately, securely, intuitively and in a familiar environment.
Ensuring security through redundancies. KVM systems offer numerous options for creating redundancies for mission-critical applications. Depending on the complexity and requirements of individual applications, the respective redundancy concept can be either relatively simple or complex. Redundancies back up either only the KVM system (FIG. 1), the computer side (FIG. 2), the console side or the entire application. Redundancy can be previously ensured by using a local switch for smaller applications.
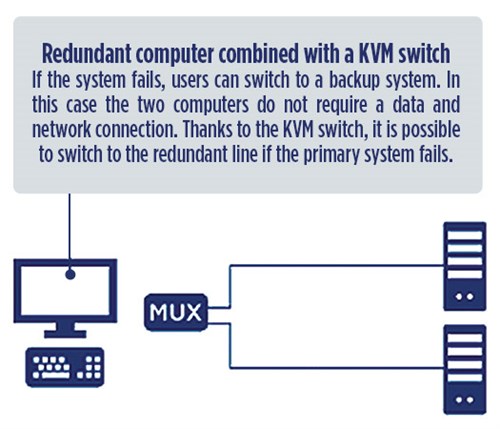 |
| FIG. 1. Redundant computer combined with a KVM switch. |
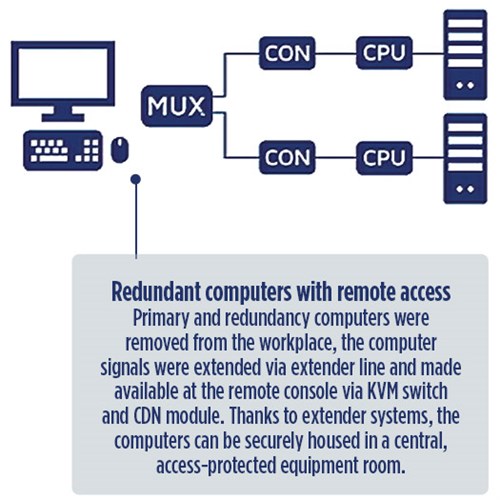 |
| FIG. 2. Redundant computers with remote access. |
Complex application redundancy. Sensitive security-critical areas and control rooms go one step further and require a completely redundant technical area and control room. KVM can provide an ideal solution for these requirements, as well.
What if Technical room A fails due to a fire in the example application (FIG. 3), and in Server room B, a KVM matrix and a server fail simultaneously (e.g., due to a software bug)? In the worst case, one of the two control rooms fails, while one of the consoles fails in Control room A.
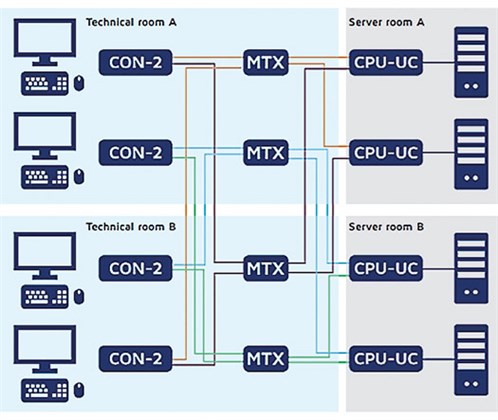 |
| FIG. 3. Technical server room. |
With a complex full redundancy of all KVM components, systems and premises, employees could still complete their work undisturbed—even in the case of such an extreme scenario.
Operating several computers on multi-screen consoles. FIG. 4 shows a multi-monitor console with four monitors, each switched to a different computer thanks to the implemented cross-display switching function. This function switches keyboard and mouse signals, whereas the video signal remains permanently connected to the corresponding computer.
 |
| FIG. 4. Multi-monitor console with four monitors. |
Operators can work on multiple computers to monitor numerous processes simultaneously. For example, if one of the CON-2 connections is interrupted, the respective CON-2 module automatically switches to the redundant matrix. Typically, all other CON-2 modules would remain on the primary matrix, which would result in an inconsistent console in which cross-display switching would no longer work.
Thanks to a “sync workplaces” function implemented in the matrix, the failed CON module automatically switches to the redundant matrix within milliseconds and takes all other CONs along. For this purpose, the admin sets up a script in advance using the configuration panel of the matrix systems, enabling the matrices’ switching equality. Therefore, all CON modules are changed to the redundant matrix, and cross-display switching still works properly. This results in consistent switching of the CON modules.
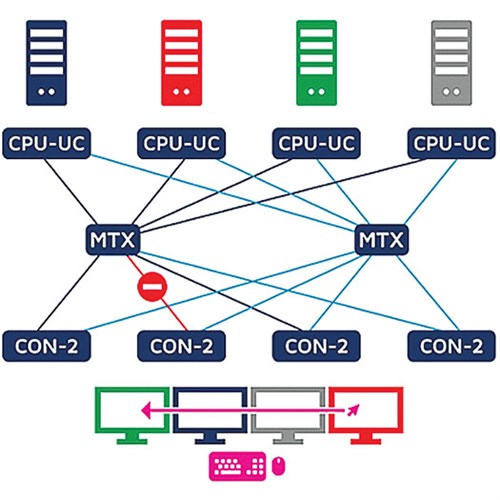
Switching equality of matrices. Two crucial advantages of redundantly designed matrix installations are the automatic switching to the redundant KVM matrix if the primary matrix fails and the automatic switching equality between the primary and redundant matrix.
In FIG. 5, MTX 1 connects Consoles 1, 2 and 3 to the blue, red and green computers. If the power supply to the primary matrix fails, CONs and CPUs switch automatically to MTX 2. Due to the instinctive switching states of both matrices, users can continue their work immediately. This is ensured by a script stored and set up in advance in the configuration panel of the matrix systems, which lets users switch the matrices simultaneously.
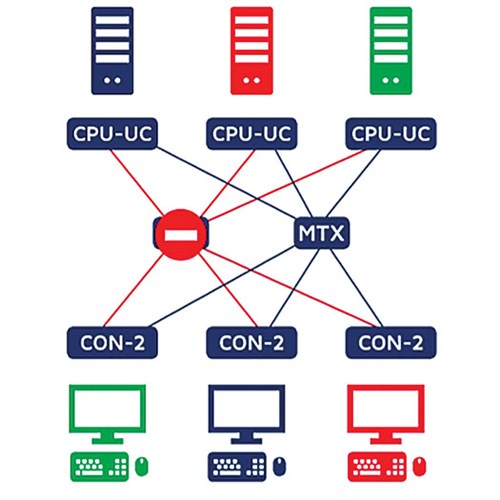 |
| FIG. 5. MTX 1 connects Consoles 1, 2 and 3 to the blue, green and red computers. |
Case study: KVM in Wiener Netze, a leading power producer maximizes availability and reliability. Major energy suppliers provide millions of people with electricity, gas and heat every day. The flipped switches must work uncompromisingly and error-free. In addition to ensuring the voltage level and load distribution, the control center employees are responsible for using and monitoring the equipment.
Complex control centers and data management systems require large computer landscapes and a wide variety of peripheral hardware. Such was the case with Wiener Netze GmbH, which provides the basic electricity, natural gas and district heating supply for Vienna, Austria, parts of Lower Austria and Burgenland. With around 2,500 employees, Wiener Netze creates, maintains and monitors the infrastructure and distributes electricity, gas, district heating and telecommunications where they are needed.
With the help of a KVM matrix switch, it is possible to decouple the complex computer technology from the workstations and outsource it to a specially equipped technical room (FIG. 6). The distance to the remote computers is bridged by corresponding computer and workstation modules, which correspond to the central matrix via CAT or fiber optic cables. These allow access to computer technology in the background as if the operators were sitting directly onsite.
 |
| FIG. 6. Technical room. |
Control room clusters on the smart campus form the security area of Wiener Netze and must remain accessible. Therefore, the highest availability and security are essential for this project. For this reason, all infrastructures in the control rooms are entirely redundant, monitored and controlled with the aid of modern technology.
All computers of the control rooms were moved to a technical room and connected to KVM matrix switches. KVM peripheral modules extend and make computer signals available at the control rooms’ workstations, each equipped with six screens. In medium-voltage control rooms, each console is provided with 10 monitors.
The high-voltage control center (FIG. 7) is the largest in the control room cluster. Upon entering, a display wall equipped with 6-m × 4-m Barco LED cubes immediately catches one’s eye. Located directly behind it is one of the technical rooms, where several 19-in. server racks are equipped with state-of-the-art equipment so that the staff in the control room can carry out their tasks smoothly and continuously.
 |
| FIG. 7. High-voltage control center. |
All control room workstations are structured similarly, making it easy for employees to change between them quickly. This way, they can still perform their usual tasks despite working on another desk.
This solution’s key advantage is that all computer sources are connected to a matrix switch, extending the signals back to the consoles. This lets employees access the required computers from any controller position.
In the central server room, a total of 40, 19-in. racks were equipped and installed, leading to immense computing power. This is where the two fully mirrored and redundant KVM matrix switches are located.
All computer sources can be switched to all workstations thanks to KVM matrices. Predefined user rights make it possible to determine which users can access which computers.
Redundancy done right. Redundantly designed IT infrastructures using KVM systems provide numerous advantages. Reliable and always available devices, including redundancies, make a KVM installation a safe investment with advancement opportunities in the future. From simple setups with extender lines to complex concepts for fully redundant infrastructures with automatic switching to backup systems or redundant control rooms, the possibilities for designing redundant structures with KVM systems and thus increasing application security are endless. GP
 |
DON HOSMER is the VP Sales Americas and General Manager at G&D North America Inc. Mr. Hosmer has more than 30 yr of experience in video, audio and data transport applications. He has extensive expertise in control rooms and application design for KVM extension products, switching systems and compression technologies over both copper and fiber cabling infrastructures. Mr. Hosmer earned a BS degree in business from California State University.




Comments